In any organization identity management becomes the biggest challenge when applications and websites increases and employees need to access all these applications and websites as per their permissions, because both (employees and organization) have to manage multiple credentials to access these applications and websites and it also leads security threads.
Single sign-on (SSO) provides the solution to overcome above issues. SSO enables employees to access all applications and websites with single credential.
MuleSoft Anypoint Platform enables Identity management to setup single sign-on (SSO) with external identity providers like Okta, Salesforce, Ping Federate and many more...
Any one of the below SSO standards may be used to configure Identity management
1. OpenID Connect: End user Identity verification by an authorization server including SSO
2. SAML 2.0: Web-based authorization including cross domain SSO
In this post we will concentrate more about SAML and its configuration steps with Okta
Objective : At the end of this blog you will learn
- How to setup SSO for Anypoint Platform using Okta
- How to create user in Okta and sync automatically in Anypoint
- How to map group between Okta and Anypoint with basic privilege's
PreRequisite
1. Okta account with Admin access --> you may create using Create Okta Account
2. At least four email IDs which will be used as users in Okta and Anypoint
3.Anypoint account with Access Management role --> You may create using Create Anypoint Account
Lets understand How SAML works ?
i. User
attempt to login Anypoint Platform using below URL https://anypoint.mulesoft.com/accounts/login/{your_org_domain}
ii. Anypoint
redirect to identity providers like Okta
iii. User
browser sends authentication request to Okta
iv. Okta
authenticates user and sends an assertion to browser where assertion may
contain username, email, group etc.
v. Browser
sends SAML response to Anypoint Platform
High Level Steps to Configure SSO using SAML
- Create Application on Okta and Provide the SAML2.0 configuration details like single sign-on URL of Anypoint and audience URI along with attribute statements and group attribute
- After configuration you will have IDP meta data which will be imported into Anypoint
- Post that login to Anypoint and then create the Identity provider and import the above IDP meta data
- At the end grant the permission to users and test the implementation
Let’s begin the actual implementation
Login to Okta and click on the
application and then Click on Create App Integration
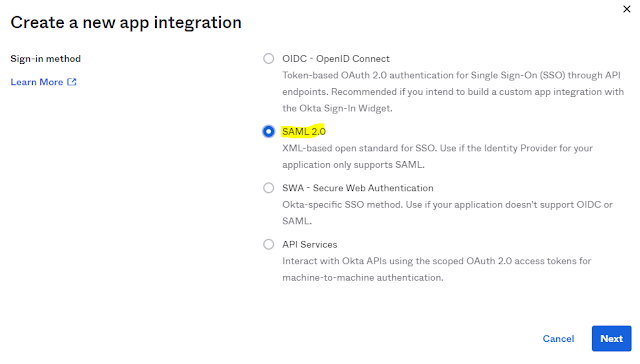
Then select SAML2.0 and click Next
Then enter the General setting details
App name: MuleSoft Okta Demo and click next
Next Configure SAML which contains two sections
Section A: SAML Setting which includes below
- General: In this section provide mainly
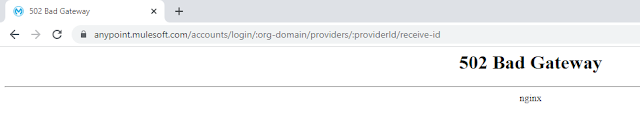
- Single sign-on URL --> The location where SAML assertion is sent with http post and its value will be https://anypoint.mulesoft.com/accounts/login/:org-domain/providers/:providerId/receive-id and this value will be replaced once configuration at both sides (Anypoint as well as Okta) completes
- Audience URI --> The application defined unique identifier that is the intended audience of the SAML assertion and its value will be {organisation}.anypoint.mulesoft.com and question is how to get anypoint organisation id. To get it login to anypoint and click on the organization as below and value will be like 9402c32b-1e47-456a-9da3-04cf4d1e7581 so complete URI will be 9402c32b-1e47-456a-9da3-04cf4d1e7581.anypoint.mulesoft.com
- Attribute statement: This is optional and it will assign the assertion values like firstname, lastname and email from okta user properties firstName, lastName and email and these values will be created at Anypoint
- Attribute name: firstname
- Attribute format: Unspecified
- Attribute value: user.firstName
- Attribute name: lastname
- Attribute format: Unspecified
- Attribute value: user.lastName
- Attribute name: email
- Attribute format: Unspecified
- Attribute value: user.email

- Group Attribute Statement: This will map group from okta having multiple users assigned with the Anypoint group, you will see more about it later in this post
At the end, get the IDP metadata and configure into service provider ie Anypoint. To get IDP meta data goto application and select the MuleSoft Okta Demo application then click on sign-on then click on View Setup Instructions like below
After clicking to View Setup Instructions, new page will open which will following details which will be configured at Anypoint
Identity Provider Single Sign-On URL:https://dev-10006408.okta.com/app/dev-10006408_mulesoftoktademo_1/exk4njibd2yAIXBCC5d7/sso/saml
Identity Provider Issuer:http://www.okta.com/exk4njibd2yAIXBCC5d7
X.509 Certificate:
-----BEGIN CERTIFICATE-----
XXXXXunu6uoxpdOW+VkA==
-----END CERTIFICATE-----
Optional: This will contain all the above three details which you need to configure in MuleSoft
Copy the content of the optional filed into xml file to configure into Anypoint else you need to provide these details manually for each related fields in Anypoint
Now login to Anypoint and navigate to Access ManagementThis error is because of Okta user is not assigned to the application "Mule Okta Demo" that you have created into Okta. So first assign the user into Okta like below
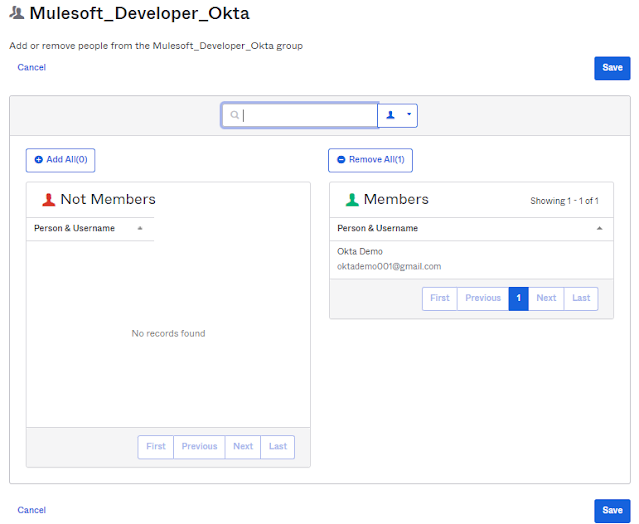
After that click on Identity providers and click on SAML Identity provider Okta and then click on Advance Setting and add the group attribute as MuleDeveloper





























No comments:
Post a Comment